Mamata Didi Ke Bolo Grievances/Suggestions Submission West Bengal : didikebolo.com
Service Name : Didi Ke Bolo
Applicable For : Residents of West Bengal
Applicable State : West Bengal
Website : https://www.didikebolo.com/en/
Didi Ke Bolo Grievances
This is a platform where the people of Bengal are being provided with the opportunity of sharing their grievances, suggestions and feedback directly to Mamata didi.

This initiative will help in bridging the existing communication gap.
How To Submit Grievances?
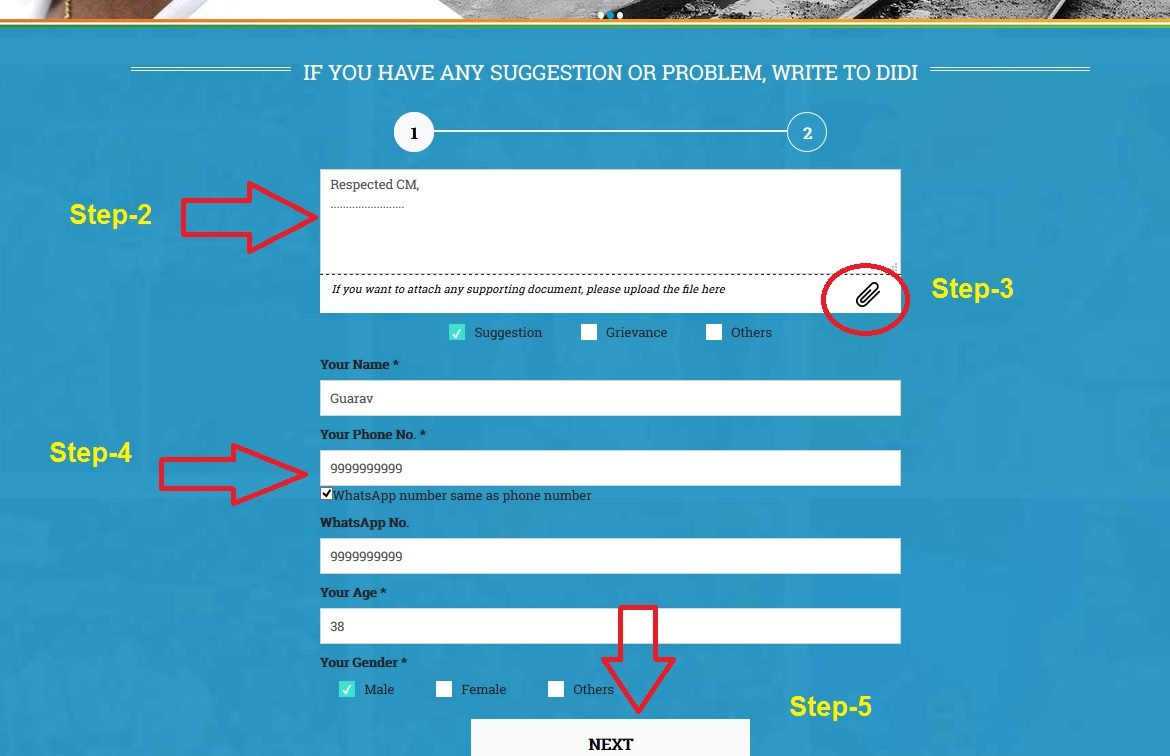
If you have any suggestion or problem, write to didi
Steps:
Step-1 : Go to the link https://www.didikebolo.com/en/
Step-2 : Enter your suggestion or problem.
Step-3 : If you want to attach any supporting document, please upload the file by clicking the “Document Attach”icon.
Step-3 : Enter your Personal Details and
Step-5 : Submit the “Next” button.
Didi Ke Bolo FAQ
1. How will my concern be handled?
Your concern/query will be forwarded to the necessary department/authority in the government for a quick response/redressal on it.
2. What is the turn-around-time for my concern?
The turnaround time of each query/concern will vary from one another. We shall be providing you a unique ID which will help you to track your concern. However, we strive to address each concern in the least possible time.
3. How will I know if my concern is addressed?
Each query/concern will be assigned a unique identification number, this will help you in tracking the status of your concern over the phone in this very number.
4. How will my personal information be handled?
We maintain extreme professional standard with the data collected, the information is used only to track down the completion status of your query/concern.
5. How can I meet the CM?
We appreciate your interest in meeting our honourable Chief Minister, kindly provide us with your details and we will get back to you when a meeting can be scheduled for the same.
6. How can I submit my supporting documents?
To provide us with your document(s) kindly mail us @ info@didikebolo.com with your unique identification code as the subject line
7. How can I register my concern in out of office hours?
Each query/concern will be assigned a unique identification number, this will help you in tracking the status of your concern over the phone in this very number.
8. How will the confidentiality of my information be maintained?
Each query/concern will be assigned a unique identification number, this will help you in tracking the status of your concern over the phone in this very number.
Securing of your data:
1.The Party has in place, standard security policies and technical measures to store in secured servers, protect the Information that is possesses by your use of the Website, from any unauthorized access, improper collection, use or disclosure, unlawful modification and illegal destruction or inadvertent loss. However, for any loss or theft of Information, due to unauthorized access to the User’s Devices through which the User accesses the Website, the Party shall not be held liable for any loss whatsoever incurred by the User.
2.The Party has reasonable security practices and has a comprehensive documented Information Security Programme consisting of operational and physical security control measures to safeguard the Information being collected.
Confidentiality:
1.It is important for you to be protected against unauthorized access, your Device. Kindly ensure that you off from the Device, once you finish using the Website. If you suspect any unauthorized use of your Device, immediately notify the Party by sending an email to the Party. You shall be liable to indemnify the Party due to any loss suffered by it due to such unauthorized use of your Device.
2.The Party shall not be responsible for any confidentiality, security or distribution of your Information by the Party outside the scope of our agreement. Further, the Party shall not be responsible for any breach of security or for any actions of any third parties or events that are beyond the reasonable control of the Party including but not limited to, governmental acts, unauthorized access to Device data and storage device, crashes, breach of security/encryption, Internet service or telephone service related issues etc.